According to Chainalysis, payments to ransomware gangs using cryptocurrency more than quadrupled in 2020, with less than 200 cryptocurrency wallets receiving 80% of funds. And, Palo Alto Networks – which claims to use data from ransomware investigations, data-leak sites, and the Dark Web, reports that the average ransom paid by companies in 2020 jumped 171% to more than $312,000. Despite being around for many years, the rise of ransomware has largely coincided with the diminished value derived from compromised personal data.
The REvil ransomware-as-a-service operation now picks up the phone to add a threatening personal touch to its exploits: “Calling gives a very good result. We call each target as well as their partners and journalists—the pressure increases significantly.” According to a published March 16, 2021 interview with a representative of REvil – also known as Sodinokibi, the group has “big plans for 2021.”
Probably the more interesting point made by this REvil representative was the answer to the following question: “Do your operators target organizations that have cyber insurance?” The answer is not much of a surprise: “Yes, this is one of the tastiest morsels. Especially to hack the insurers first—to get their customer base and work in a targeted way from there. And after you go through the list, then hit the insurer themselves.” This is the first confirmation from an actual ransomware gang that they target cyber insurance policyholders.
Articles from the Associated Press and ProPublica years earlier suggest that cyber insurers were inadvertently driving up ransomware attacks but neither outlet provided any hard facts to back up their supposition. Indeed, a leading broker took the natural counterpoint: “[A]lthough no one wants to support cyber criminals, organizations are forced to weigh the option of paying ransoms against the risk of operational disruptions that could last weeks or months and cost far more.”
It was never hard to imagine, however, that buying cyber insurance actually places a target on those companies who buy it and do not likely have the security resources necessary to stop ransomware gangs – especially given carriers may be inadvertently providing a roadmap to their house. Indeed, last year one major cyber insurer was purportedly targeted by the Maze ransomware gang. And, as of March 2021, there were at least two ongoing investigations involving attacks on major cyber insurers. Unless things change, it will only get worse for insurers and brokers given they are the new holders of the crown jewels.
One tactic that can impede the current claims challenge facing the industry is building on what was recently begun by AIG – a thought leader in this space for over two decades. In January 2021, AIG became the first lead cyber insurer to require ransomware co-insurance across the board – mandating that insureds share in paying a ransom payment. Following this lead, the larger markets began hardening on price and their underwriting requirements. Other markets immediately began to take advantage – only temporarily repairing the holes in the dike. As pointed out by Inside P&C: “The retrenchment of capacity and continued upward pricing pressure also continues a reordering of the market in which some of the largest names in US cyber insurance cede market share to upstart InsurTechs.”
Despite the fact cyber insurer MGAs are heavily funded and are now grabbing as much market share as they can, they still use paper backed by the largest reinsurers in the world – who frankly probably care more about their own profits rather than the market growth strategies of unrelated companies. In other words, any retrenchment may also eventually hit the MGAs when treaties get renegotiated.
Retrenchment is a good idea but will not be enough to fully address the problem. The best way to solve this problem is to do exactly what the FBI has said for years – do not pay the ransom. An October 2020 OFAC Advisory buttresses this “do not pay” advice by warning insurers against making ransomware payments to those on the OFAC list. In other words, law enforcement would prefer that ransomware payments not be made and it may ultimately be in everyone’s best interest if such payments are self-insured – making it much less likely they will actually be paid.
This is not K&R coverage where lives are typically at stake. Once the ransomware gangs recalibrate knowing there is no available insurance payment, the incidents will resemble earlier times, namely demands that are less frequent and for lower amounts. These threat actors want to go in and out as fast as possible given they know that the data itself likely has very little real value on the Dark Web – it’s the urgent threat of release that has exploitive value. If there is no expeditious insurance payment, the actual value of the target diminishes.
Insurance dollars are actually better spent helping insureds bolster their security rather than the coffers of criminals – especially because even with a payment there is no guarantee that data would be properly decrypted or that a Dark Web release or sale would not take place. There is much that can be done to assist insureds improve their risk profile and better avoid ransomware exploits. Some very basic steps include developing trusted partner relationships with vendors and law enforcement before an incident takes place; retaining a security expert to evaluate the current readiness profile; providing consistent education and training of staff; and developing or updating a Business Continuity Plan.
On a more technical level, full and incremental backups should be consistently performed like your company’s life depended on it; weak passwords of service accounts should be removed; system logs should be maintained and monitored; employee access to sensitive data and information limited; operating systems and applications timely patched; users with admin privileges evaluated to ensure passwords are strong and secure; system safeguards such as Windows Defender Credential Guard deployed; port connections monitored and unnecessary ones removed, etc., etc., etc. The relevant protocols all have a common goal – harden security sufficiently so that the bear decides to run after the slower runner. If everyone ends up becoming a fast runner, the hungry bear will eventually tire of the chase and just eat something else for food.
With a robust cyber insurance policy in place, most every resource necessary to assist a ransomware victim is already available to an insured. By focusing on these other valuable first-party coverages, improving an insured’s risk management profile, and curtailing ever increasing payouts to criminals, the industry will continue with its meteoric rise.

UPDATE: March 25, 2021
On March 24, 2021, CNA publicly disclosed that it sustained a cybersecurity attack. As of March 25, 2021, the following is the only information found on its website:
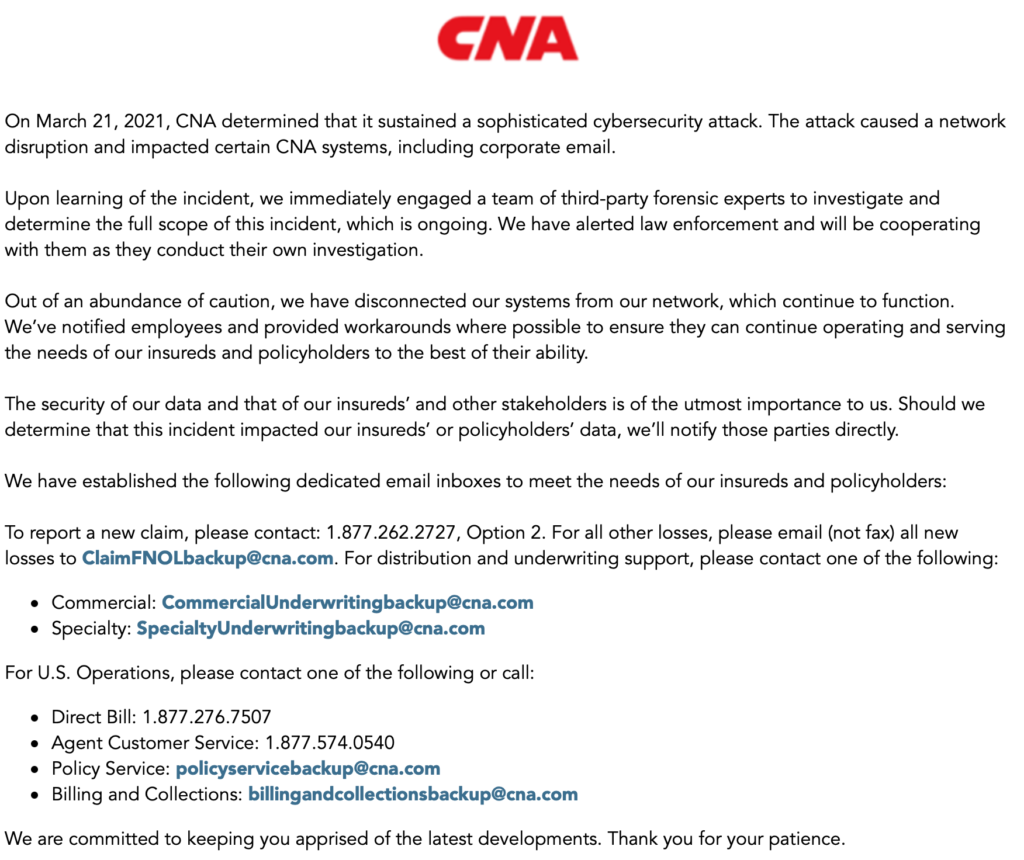
UPDATE: May 10, 2021
The day before the Colonial Pipeline ransomware attack went public, global insurer AXA announced it would cease writing cyber-insurance policies in France that reimburse policyholders for ransomware extortion payments. This is hopefully the start of a much larger trend.
UPDATE: May 12, 2021
On May 12, 2021, security experts labeled as “absolute stupidity” comments regarding the payment of ransomware that were emanating from the White House. A few days prior, the White House’s Deputy National Security Adviser for Cyber, Anne Neuberger, had given the private sector a complete free pass regarding the payment of ransoms: “And they have to just balance off, in the cost-benefit, when they have no choice with regard to paying a ransom.” Unfortunately, this position directly contradicts the long-standing position of the FBI and numerous other government agencies.
UPDATE: December 1, 2021
On November 18, 2021, North Carolina relied on its Operations Appropriations Act of 2021 to add a new article to Chapter 143 of the State’s General Statutes which now reads in part: “No State agency or local government entity shall submit payment or otherwise communicate with an entity that has engaged in a cybersecurity incident on an information technology system by encrypting data and then subsequently offering to decrypt that data in exchange for a ransom payment.” This is the first effort by a governmental entity to bar ransomware payments.









