While many business owners recognize the importance of maintaining their Cybersecurity Hygiene and protecting their Intellectual Property (“IP”), they are often too pressed for time and money to implement any serious plans of action. There are ways to improve your cybersecurity and IP postures without breaking the bank or ignoring revenue goals.
Be proactive and not take for granted good cybersecurity hygiene exists in your company. To start this exercise, every business owner should at least have someone review the readily available free resources on the subject. For example, the U.S. Small Business Administration (“SBA”) has online resources dedicated to informing small businesses on how to bolster their cybersecurity. And, the National Institute of Standards and Technology (“NIST”) helps companies who admittedly have modest or no cybersecurity plans in place by offering to “kick-start their cybersecurity risk management strategy” with the NIST Cybersecurity Framework (CSF) 2.0.
Tip #1: Choose WordPress for your website. After reviewing free resources, business owners can determine which direction to turn when it comes to preparing for the worst. For example, you may want to start out by looking at one of your main sources of credibility in the marketplace – your website. A secure site will always score higher on SEO than an insecure site – which makes it crucial for business to focus on reputational integrity and protection of customer data. The WordPress platform is extremely popular with small business owners given its content management system allows owners to easily upload and modify content – without the need for a developer charging for every edit.
Given that a large portion of the Internet is using WordPress, Corporate websites built using WordPress allow for secure custom shops and can securely mesh with your own separate e-commerce shop built using tools such as Shopify.
Some WordPress tips include keeping WordPress on auto-update to ensure all security updates are in place as soon as possible; choosing a mature template with many thousands of downloads that has been security tested over a long period and routinely updated; limiting the use of Plugins to those essential for WordPress security, including WordFence (or a similar firewall/scanning plugin) and WPS Hide Login (or similar plugin that hides the default login URL frequented by hackers) because many incidents are directly tied to insecure plugins – those that may have not been updated in years yet are still active on your site; and making sure you install an SSL (Secure Sockets Layer) Certificate allowing for encrypted HTTPS communications between site and browser.
The last tip is especially important given Google’s Chrome browser and Brave’s browser have long warned users when a website does not use this HTTPS protocol – a warning that likely causes potential visitors to not even visit the site. The Really Simple SSL plugin can help ensure that this is easily done. Many hosting companies provide a free SSL certificate so getting the plugin will make this an easy fix if needed.
Tip #2: Practice good security hygiene by using passwords that include upper case letters, numbers, lower case numbers, and symbols that total no less than 10 characters. Keep the password in a safe place if you cannot memorize it and only use it for your website. As well, deploy two-factor authentication to make it that much more difficult to get in the website using the front door – Authenticator is an excellent app for 2FA purposes but there many to choose from. When it comes to passwords, the strongest chain of defense can only be as strong as its weakest link.
Tip #3: Remind all employees never to click on links in emails – even if they seem legitimately from companies you do business with, including lawyers and accountants. As for the most basic of “basic training”: Don’t open or click on anything that looks suspicious. Again, it is much more difficult for hackers to launch an exploit without walking in the front door and they can’t come in if you don’t open the door. In other words, never click on a link, file or image from an untested source or unknown URL. The extra seconds it takes to confirm the actual sender of an email message or owner of a website is well worth the time.
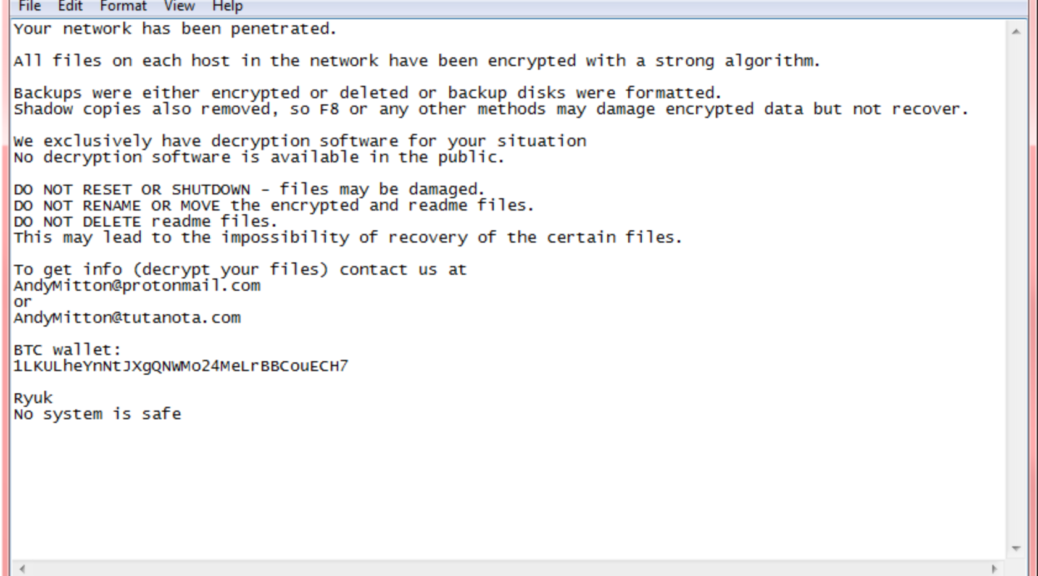
Tip #4: Safeguard against Ransomware attacks. Given credit card data and account information has long been dirt-cheap to buy on the dark web, hackers now combine social engineering, e.g., well-crafted targeted emails using publicly available information, including emails of licensed professionals, with botnets usually tasked with promulgating spam and searching for vulnerabilities. The result is a ransomware attack that can cripple a business unless Bitcoin is transferred to a specific account.
The FBI has long suggested firms focus on a variety of basic prevention efforts – in terms of awareness training for employees and technical prevention controls, as well as the creation of a solid business continuity plan in the event of a ransomware attack. And, after a ransomware attack is suspected, victims should immediately contact the local FBI field office and report the incident to the Bureau’s Internet Crime Complaint Center.
If a firm wants to immediately enact a more proactive approach, however, there are certainly additional very basic policies and procedures that can be put in place right now to help avoid a ransomware exploit: (i) block executable files (such as “.exe” files) and compressed archives (such as zip files) containing executable files before they reach a user’s inbox; (ii) block the use of thumb drives; (iii) mitigate against social engineering exploits by providing employee online training that is continuous and targeted with services such as KnowBe4; (iv) make sure whoever is providing you with IT support has a software patch management plan in place; (v) regularly back up data with media not connected to the Internet.
Tip #5: Apply for Cyber Insurance. Given the recent massive spike in small business insureds being specifically targeted, price hardening and onerous underwriting requirements have been the norm for cyber insurers. While it is way too soon to turn in the towel on small business cyber insurance, some of those allocated insurance premium dollars might also be spent on bolstering security as well as lower cost/higher deductible coverage.
One key attribute of any cyber insurance should be the technical vendors and legal counsel associated with these carriers. Cyber insurance will also always serve a vital role in helping small business owners deal with ransomware attacks by offering the benefit of an underwriting process so that businesses can better understand their vulnerabilities and potential strengths – all without the need of hiring a consultant or paying any fees. Indeed, an insurer acting as a trusted partner may even assist a potential client obtain compliance with an insurer’s cybersecurity standards before the insurance is even purchased
Protecting your most valuable assets – your intellectual capital, is well worth the effort. Whether it’s how your employees conduct business, which clients you do the most business with, how you service those clients, or how you communicate with clients and employees, intellectual property is wrapped around all of it.
Tip #1: Your know how needs confidential treatment. Your client list and how your clients are serviced constitute your “know how” or more commonly “trade secrets” that must be kept confidential – once they become public any protections you may have had will evaporate. The use of non-disclosure agreements with third parties is essential – as well as ensuring your employees understand this fundamental concept. Using well-written contracts with clients will also help ensure your know how is protected.
Tip #2: Your brand, sales and marketing brochures, and training materials are trademark and copyright protected. Even a small company with no employees can have a robust brand built over many years – and found predominantly on the company’s sales and marketing materials. All that is necessary for local common law protection is that it be in use to identify specific services or products. To obtain nationwide protection and added damages for infringement, the mark should seek federal registration using the USPTO.Gov website. Similarly, the product brochures created from scratch are copyright protected as soon as they were created but have enhanced protection when registered at Copyright.Gov.
As you review the content and systems powering your business — everything from the company names to the use of training materials — you will quickly appreciate how much value goes unguarded. Consulting a legal expert or learning how to protect your trademarks and copyrights may not be quick or glamorous, but it will give you something longstanding: ownership of an intangible asset, leverage, and peace of mind.
Tip #3: Plan for the sale of your business by incorporating these best practices. According to the SBA, more than half of the nation’s small-business owners are over the age of 50, and approximately 21% of the US population were born before 1964. And, according to one study, baby boomers owned about 51% of the privately held businesses in the United States, which is about 3 million businesses valued at $10 trillion dollars. Unfortunately, founders typically defer addressing the fact that they will one day be too old and tired to manage a successful business.
When no one in the family wants to take over your business there are only two options, close shop or sell to a willing buyer. One metric used in valuing businesses is tied to the company’s ability to scale based on its protected intellectual property assets. In other words, sustainable growth is not always about making more — it’s also about being able to protect what you’ve already built. After deploying the right practices, support system, and mindset, a successful entrepreneur can go from vulnerable to vigilant — and nurture a business that’s built for selling.